After my latest article was published last week, I received feedback from some of my readers asking me for clarification of how the stolen certificates situation I talked about in it translated to the average Joe/Jane user. What would he/she run into and what can he/she do?
Let’s see how it would work in a real case scenario. Let’s say, for example, you want to sign in to your gmail email. You’d go to a secure (encrypted) webpage, like
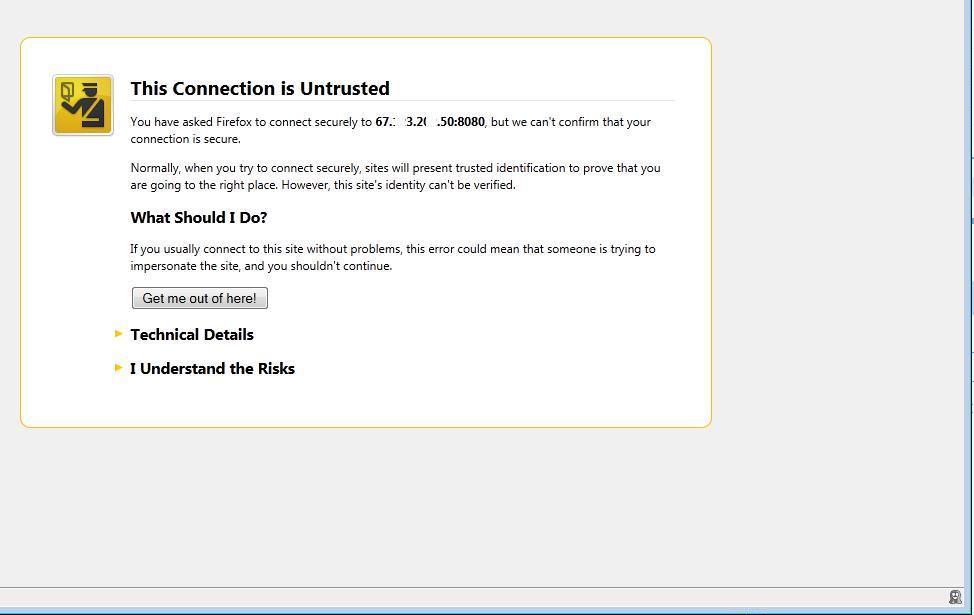
And from there provide your email address and password. But even before you do that, as soon as you click on the above link, your browser will check the certificate presented by the website, and thus corroborate that indeed, the website is legitimately what it purports itself to be. This all occurs behind the scenes, so to speak. The user does not see this process. However, if for some reason the certificate is expired, is different than expected or contains any other outpoints, the browser will alert you. In Firefox (for example), you might see something like:
You would then be able to avert the impersonation. And that’s how certs help you.
Now, if a cert is stolen and used in, let’s say, a phishing email, and you click on a link of what seems to be a gmail login, but it’s something else, AND it is using the stolen cert, you would not get the alert and thus not realize these are not the androids you’re looking for (Go see Star Wars Episode IV if you don’t get the reference 🙂 ). And so you sign in and thus give the malicious hackers your credentials.
That’s just one possible way of how stolen certs could be used for malicious purposes.
I mentioned in my last article Windows XP and Server 2003 users were the most likely to get affected. Microsoft has just released a Windows Update (KB2607712) that permanently blocks all certificates issued by DigiNotar. The update should be available to you if you have automatic updates enabled in your computer. If you don’t, want to install it manually, and know what you’re doing, here’s the link to it:
http://support.microsoft.com/kb/2607712
If you have any questions, don’t hesitate to ask.