As covered earlier in this article, Solid State Drives “don’ts” include the advice not to defragment them, for technical reasons. But Diskeeper Corporation, the makers of the defragmenting software with the same name, have claimed they have a product that not only is not detrimental to a solid state drive, but that specifically benefits them. The product is called Hyperfast.
Since I like to put claims like the above to the test, I decided to download a trial of Diskeeper Pro 2011, and see what it can do for the 9 months old Solid State Drive in my Windows Vista based laptop. This laptop is my main computer. All my web browsing, email handling through Outlook and even its SQL server based Business Contact Manager are handled from this laptop. So 9 months of constant use with no defragmentation whatsoever should make for some good wear and tear. Let’s see what Diskeeper can do for it now.
I of course have some saved screen shots of the solid state drive’s performance graph from when I got it and it was brand new, and I recently took new ones when handling another aspect of its optimization. So, we have the before pictures. Let’s see what the after pictures look like. But first, let’s install and run that Diskeeper software.
I installed and launched Diskeeper Pro 2011 (which includes Hyperfast). To be honest, it was a little confusing for me to navigate around, so I know the average user will probably be a little lost. But I digress. Or maybe not, since the point is, I wanted to make sure Hyperfast was enabled for my solid state drive, and it took a bit of looking around to do so. OK so Diskeeper knows my hard drive is a solid state one. Awesome. Now let’s have it optimize it, using all recommended settings, and then we’ll do a test or two to see if any improvements in read/write performance.
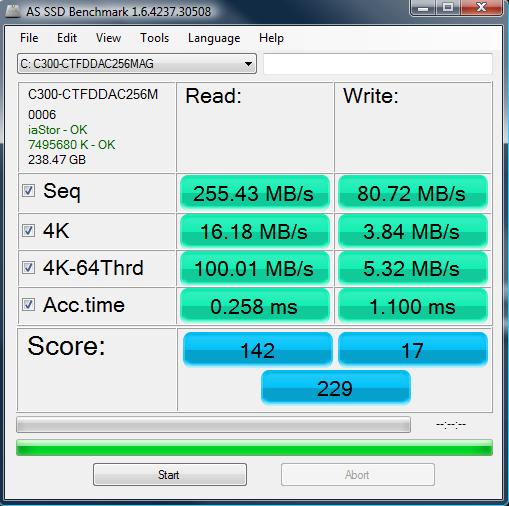
After letting it operate overnight, my solid state drive became “optimized”. So now for the speed performance tests. Although I traditionally use HD Tune to test the performance of hard drives, this time I used “As SSD”, because it’s reportedly a better benchmark for solid state drives. The numbers in the Score section are the ones to look at. This is the before-using-Diskeeper results:
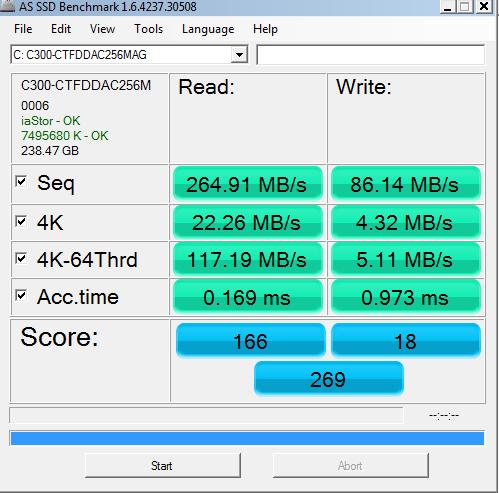
And here’s the after-using-Diskeeper one:
I must confess I was surprised to see the outcome of these tests. My initial guess was there wasn’t going to be an improvement or very little, if any. Instead, well, the numbers speak for themselves. Slight improvement in write times, considerable improvement in read times, for an overall improvement of the total score from 229 to 269. So while not as wild as the performance increase results reported by Diskeeper, there is a definite benefit from using Diskeeper’s product on a solid state drive, based on the above results.