We are now roughly at the midway point between when Windows 10 Technical Preview was released (at which point I published my first impression about it), and when it’s supposed to be released in its final (RTM – Release to Manufacturer) version. There have been quite some changes about how it works, and there are more changes to come in the following months before its final version is released.
In my opinion, there is more than one type of public for this new Operating System and therefore Windows 10 will have different reception of it, depending on the type of public that looks at it:
First there’s the type of public that is not fond of changing operating system versions every few years. They liked XP and even Windows 7 was too much of a change (not to mention Windows Vista). For them, Windows 8 or Windows 10 will look similar enough (and too different from what they’re used to) to be liked. If they haven’t moved from Windows XP to Windows 7 yet, I suggest they do, as soon as possible. If they have moved on to Windows 7, I suggest they stay there for now as for as long as they can (maybe up to a few years).
Then there’s the type of public that can adapt to new versions of operating system being released every few years, but are not fond of lost features or buggy new features. They were able to move from Windows XP to 7 and even Vista in between, and can sort of make Windows 8 work. They will probably like Windows 10. If they are presently with Windows 7, they can consider moving on to Windows 10 within the next year or two. If they’re stuck with Windows 8 right now, they should upgrade as soon as Windows 10 is released.
Finally there’s the type of public that simply can make things work, no matter what. They will like Windows 10 as well and can move on from 7 or 8.
For those who are curious and haven’t had a chance to take a look at the current Windows 10 screens as they look at the time of this writing, here’s a sneak peak:
As you boot up, the initial screen looks the same as in Windows 8:
Unlike Windows 8, once you log in Windows 10 goes into the traditional desktop view:
Notice there is a fusion of the old style Start menu (on the left) and the Windows 8 style Start menu (the tiles on the right):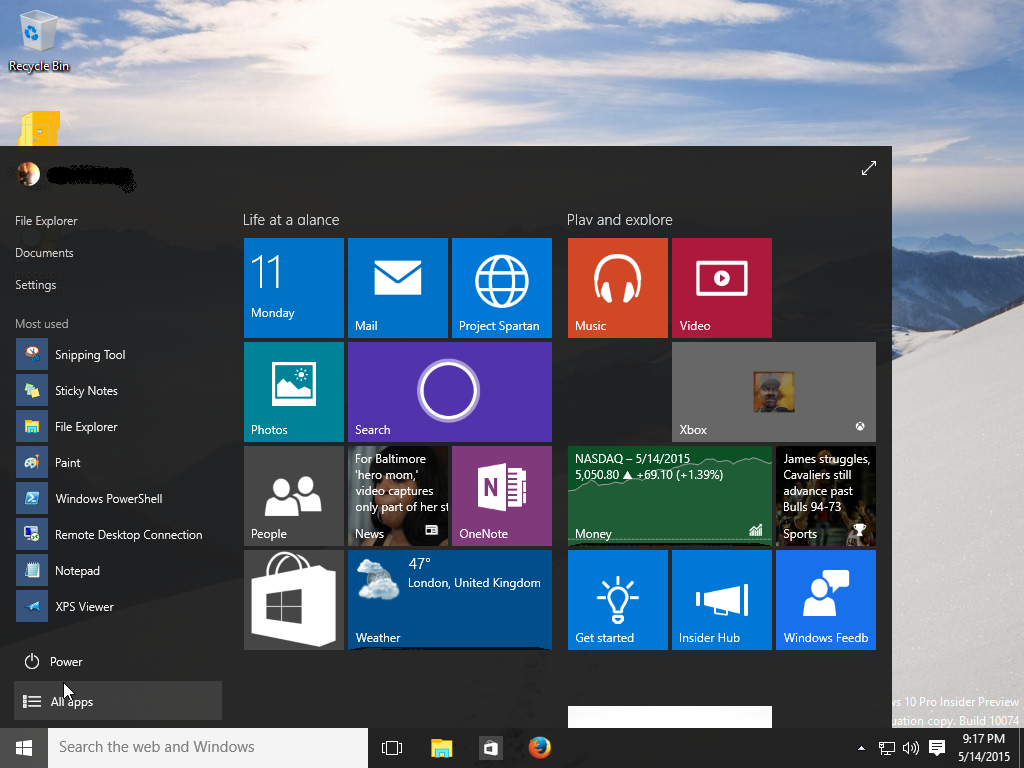
You can, however, click on the upper right of the start menu and expand it to become full screen, if you fancy the Windows 8 style better:
Notice that the background is still somewhat visible, in a hint of the Aero display theme that was used in Vista and Windows 7 and sort of died in Windows 8.
Careful readers will notice there is a tile in the above screenshot called Project Spartan. That is the code name of the new browser set to debut as the default web browser with Windows 10, and that will make Internet Explorer a secondary, backup browser. The name itself is not final and apparently is changing to Microsoft Edge.
The search function and other Windows apps are being enhanced by using Windows personal assistant, the chatty Cortana, the voice powered assistant whose name was taken from the AI – Artificial Intelligence – character in the famous video game Halo.
In short it seems Microsoft is seriously trying this time to come with an Operating System that will unify all computing devices, be it a traditional desktop, a laptop, a tablet or a phone. There are other features being developed as you read this, and some more are in the works for coming months. I’ll be following up closely on those and how Windows 10 develops, and will update again before the final release date, currently set for the end of the year.