Love that scene in Scarface. But that’s not what this is about. I recently got a Solid State drive for my laptop and wanted to share the improved performance test results with my readers.
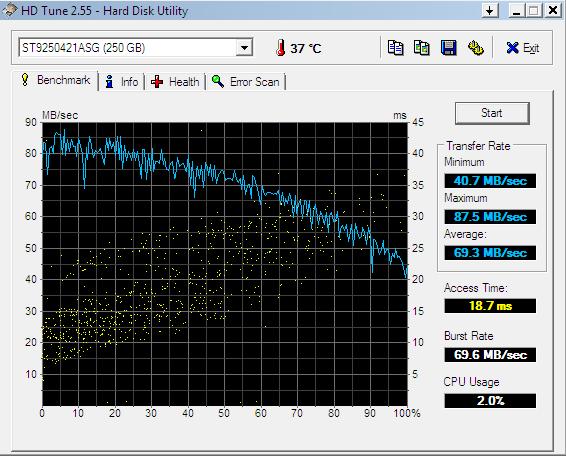
The program I used for benchmarking was HD Tune 2.55. I tested the computer both in normal and in safe mode, but I’m only posting the results gotten in safe mode, because they are the ones that I consider more reliable, since in safe mode the computer is only running the most basic programs and other software won’t interfere by using the hard disk while it’s being tested. Anyways, here’s the results of my “traditional” hard disk drive:
The blue line in the graph represents the data transfer rate over the course of the test. It fluctuated between 40 and 87.5 Megabytes per second, with an average of almost 70. Not bad for a traditional hard disk, especially since it belongs in a laptop. But now let’s see the same laptop, with a solid state drive instead of the traditional hard disk drive:
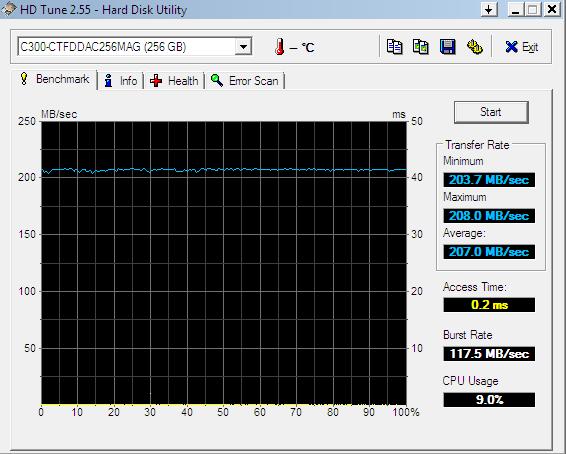
You can immediately see from the graph that this is a very different animal. The data transfer rate was between 203 and 208 Megabytes per second! Very impressive. And look at the access times! 18.7 milliseconds for the traditional hard disk drive against 0.2 milliseconds for the solid state drive!
As covered in earlier articles, a computer is as fast as its slowest component. And with the way different components have evolved over time, the secondary storage device (hard disk drive) has become the slowest component, generally speaking. But now, with the newest generation of solid state drives, there’s been a step forward towards a more balanced performance of all components.
How does this translate in the actual, normal, everyday use of the laptop? When starting the computer, from the moment the power button is pushed to the moment when the Windows login screen is available, the time went from 80 to 42 seconds! similarly proportional many applications and files were opening that much faster. It is without a doubt the single most noticeable upgrade a computer can get (as long as it’s not too old). Again, especially true for portable computers.
The only thing that is not small and compact about these solid state drives is the price. True, the one I got is (presently) the second fastest in the world, and at its biggest available size. But I could have bought a low-end, basic laptop with that money. So as usual you have to pay to play. Yet with how expensive it was, I feel I got my money’s worth. AND when I upgrade to a newer laptop, this solid state drive is going into it.