So here I was, minding my own little business this morning, when I checked my email for the first time. As I went through the unread emails, I found one from “eFax Corporate [message@inbound.efax.com]”. I checked the detailed information about that email and it actually seemed legit. Kaspersky had labeled the email as probable spam, but that was it. Nothing else out of the ordinary. And of course, the email had an attachment, compressed. So I decided to look into it.
I raised all my defense mechanisms to the highest, and proceeded to decompress the file that came attached to that email. It turned out to be a program, not a document. I scanned it with Kaspersky. Came out clean. Next, and this is the kicker, I submitted the file to a website that scans it against FORTY SIX different antivirus engines. All the brands you might have heard about and then some. How many of these antivirus engines identified the file it as malicious? ZERO! NONE! Unbelievable. I’m not kidding. Look:
| Last Scanned: |
2013-08-29 16:24:27 |
| MicroWorld-eScan |
Not Detected |
| nProtect |
Not Detected |
| CAT-QuickHeal |
Not Detected |
| McAfee |
Not Detected |
| Malwarebytes |
Not Detected |
| K7AntiVirus |
Not Detected |
| K7GW |
Not Detected |
| TheHacker |
Not Detected |
| NANO-Antivirus |
Not Detected |
| F-Prot |
Not Detected |
| Symantec |
Not Detected |
| Norman |
Not Detected |
| TotalDefense |
Not Detected |
| TrendMicro-HouseCall |
Not Detected |
| Avast |
Not Detected |
| ClamAV |
Not Detected |
| Kaspersky |
Not Detected |
| BitDefender |
Not Detected |
| Agnitum |
Not Detected |
| SUPERAntiSpyware |
Not Detected |
| Emsisoft |
Not Detected |
| Comodo |
Not Detected |
| F-Secure |
Not Detected |
| DrWeb |
Not Detected |
| VIPRE |
Not Detected |
| AntiVir |
Not Detected |
| TrendMicro |
Not Detected |
| McAfee-GW-Edition |
Not Detected |
| Sophos |
Not Detected |
| Jiangmin |
Not Detected |
| Antiy-AVL |
Not Detected |
| Kingsoft |
Not Detected |
| Microsoft |
Not Detected |
| ViRobot |
Not Detected |
| AhnLab-V3 |
Not Detected |
| GData |
Not Detected |
| Commtouch |
Not Detected |
| ByteHero |
Not Detected |
| VBA32 |
Not Detected |
| PCTools |
Not Detected |
| ESET-NOD32 |
Not Detected |
| Rising |
Not Detected |
| Ikarus |
Not Detected |
| Fortinet |
Not Detected |
| AVG |
Not Detected |
| Panda |
Not Detected |
I started to think, maybe the file wasn’t malicious after all; Then I laughed at myself for thinking that. Since I felt a little lazy, rather than firing up my test computer to analyze the program behavior when opened in real time, I submitted the file to a service that does that for me online, and then emails me the complete analysis results. I got an email back and…
I’ll spare you the technical details but that little file reminded me of that scene in the movie Transformers where a cell phone is radiated with the special beam of energy that animates it and the cell phone transforms into this destroying little machine inside a secure container; It goes berserk. That program did all kinds of things, from creating files, to deleting the original program, establishing network connections, modifying the registry, on and on. Definitely malicious.
This was the first time I’ve seen a program that is obviously malicious get a 0% rate of detection when scanned with those 46 antivirus engines. I had seen 6/46 or even 4/46, but never 0/46! Must have caught a really fresh one that no one has had the time to label as malicious and incorporate to the antivirus black lists so it gets detected.
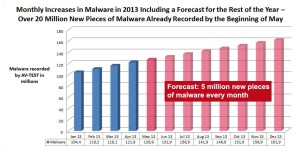
But my point and the moral of the story is that, unfortunately, and as I’ve said in several occasions, traditional antivirus detection methods are just not enough to catch all malware anymore. It takes the full 4-prong security model laid out in my pivotal article, written a while back, to ensure the best chance at remaining immune to most attacks.